There is no such thing as a piece of software that is completely secure.
When it comes to WordPress, that point is especially true as it’s a highly-exploitable platform. Thanks to the third-party support through plugins, themes and custom code settings exploitability is increased even more. This is unfortunate, because WordPress is one of the most widely used content management systems out there. There are a few rules how to avoid those kind of problems. For example, try to use only those plugins that are already checked. If you want to have a website theme, buy it from a place you know is good. However, in the very root of the problem, it’s not so simple.
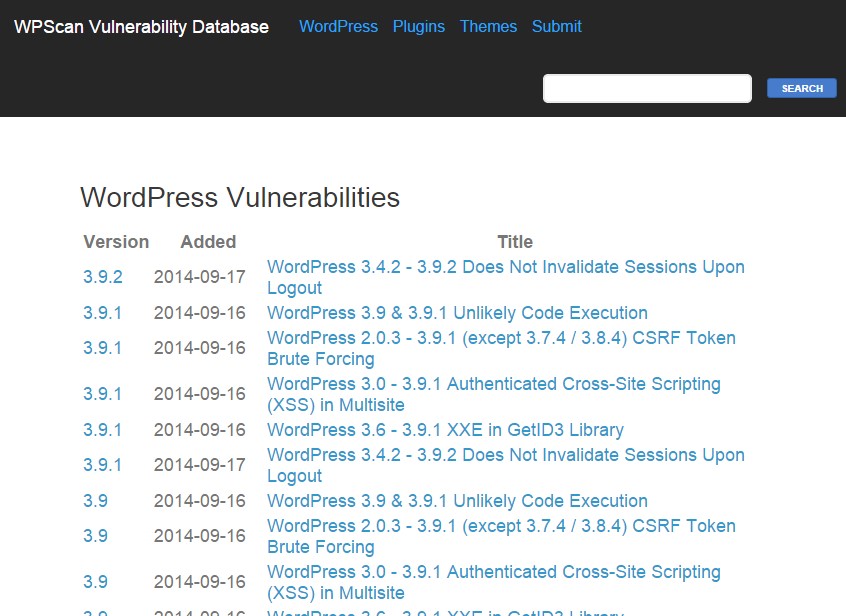
Ryan Dewhurst, a British security researcher, has created a publically accessible database that lists any and all discovered vulnerabilities in WordPress. The WPScan Vulnerability Database adds a crucial element that has otherwise been missing from the platform. Resourceful individuals can use this data to lock-down and secure their WordPress powered sites or make sure themes they are using are not compromised.
Dewhurst created the database with £5,000 awarded by BruCON, a non-profit security conference that is held in Belgium every year. He used his WordPress scanner tool – which the database is named after – to pull vulnerability data which is now listed on the official site.
“This should be useful to security professionals (ethical hackers) to be able to look up what plugins, etc., have vulnerabilities during penetration tests. It should also be useful to people who run WordPress web sites to check if they are vulnerable. Also it may help in shaming third-party developers to do a better job in future in terms of the security of their software.”

What Does This Mean for WordPress Users?
There are two ways this database can be used, for good or bad.
Worst case scenario: malicious parties use this information to hack into vulnerable WordPress sites. There are many reasons why they would do this, from collecting personal data to gaining control over the site resources or domain. That said, it’s more likely (as Dewhurst mentioned himself) that those malicious parties have better means of discovering vulnerabilities. Skilled baddies know their way around the backend of WordPress already.
The other scenario is that it can be used to further secure WordPress installs for everyone. Perhaps a developer will release an unofficial patch of sorts that fixes many of the problems in the database, at least when it comes to the core WordPress experience. A great deal more of the vulnerabilities come from plugins, but those would have to be fixed by their respective developers.
There are a number of WordPress vulnerabilities that have gone unpatched by the official team, because they “don’t believe the risk of the issue is worth the effort in fixing it”. Which is another way to say they don’t want to waste their time. In comparison, there are 29 pages of vulnerabilities dedicated to plugin problems, while there are only three dedicated to core problems.
What a Vulnerable Plugin Looks Like
The WordPress plugin Custom Contact Forms, was found to be vulnerable in a big way. The security flaw allowed attackers to gain access to the website and download the owner’s database remotely without ever having to provide the proper authentication or security information. In other words, after being installed and activated it could render a website completely vulnerable. That’s pretty disconcerting especially since the plugin has more than 640,000 users across the internet.
The security firm Sucuri tried getting in touch with the plugin’s developers, with no result. Naturally, they published a blog post, stating “due to the unresponsive nature of the development team, we’d encourage you to pursue other sources for your WordPress form needs.”
How Can I Use This Information?
If you happen to be a developer, you can use this database information to patch your install or plugin and protect your site better. If you’re a web admin with no development experience, that’s okay. You can use this information to steer clear of third party plugins that might open up your WordPress site to hackers (and check those that are popular).
In the end, there is no way to completely prevent your site from attacks – where there’s a will there’s always a way. However, you can do everything remotely possible to mitigate those attacks by securing your WordPress site.
If you’d like more information on the matter you can head on over to Forbes original coverage, or Dewhurst’s official site.
Use WPScan to Detect Native Vulnerabilities
You can use the WPScan plugin to detect native vulnerabilities on your website. Install and run the plugin and it will analyze your entire database looking for ways attackers could gain access. Mind that you’ll need developmental knowledge to patch any of the issues that are discovered, unless they relate to a plugin. If a vulnerability has been attributed to a plugin, you could simply uninstall it and look for an alternative.
It’s worth noting that plugins can create threats and lower security overall. That’s why many web designers recommend developing your own site content. Themes can also cause issues, especially when they implement new functionality.
It would behoove you to invest some time better securing your site, before you run into a serious problem.



Thanks for the article. I will definitely be using that database to make sure my clients are as secure as possible.
Your way of explaining is great, as well easy for readers to understand. It is very useful and informative post to all wordpress developers. Keep up sharing such great post with us.